Ghidra Dynamic Emulation Plugin
Dynamic emulation through the Malcore API
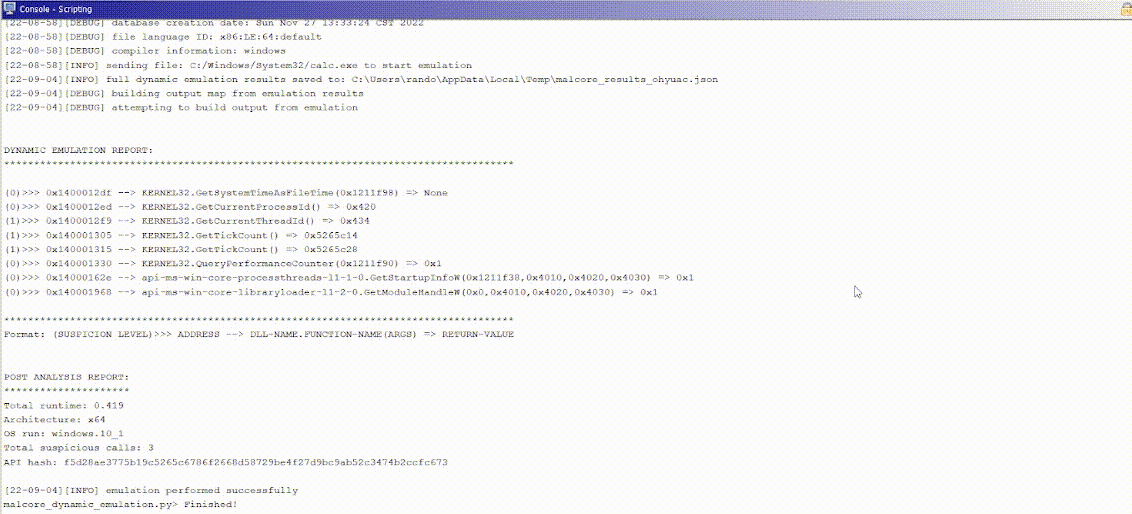
Malcore now supports Ghidra as we enable you to perform dynamic analysis within Ghidra without the need for a sandbox:
What does this do?
Ghidra is a reverse engineering framework developed by the NSA and released to the public. It allows users to create custom plugins and implement them into Ghidra for use. This plugin allows users a quick and efficient way to perform dynamic analysis while performing reverse engineering. It will provide you with Windows API call information, the arguments passed to the API function, and the return value of the call. It will also provide you with a post analysis report that will give an amount of potentially suspicious calls, file architecture, as well as an API hash.
Key Features:
Dynamic emulation of files
Function call coverage
Loaded library coverage
API hash
Installation:
Installation is simple and a detailed explanation can be found on the Github repository. In order to use this plugin you must have a Malcore API key. To get yours register on Malcore today.